Container Vulnerability Assessment Simplified
Why Is Container Vulnerability Assessment Worth Your time?
- Isolation Flaws
- Vulnerable Container Images
- Insecure Configuration of Components
- Kernel-level Vulnerabilities
- Insufficient Authorisation
- Lack of Runtime Security Monitoring
- Host-side Vulnerabilities
- Untrusted Containers
- Broken Access Control
- Exposed and Compromised Secrets
- Insecure Inter-Container Communication
- Inadequate Container Encapsulation
Enquire for Containers VA
Benefits of Container Security Testing
Containers are a big part of modern IT, but they are also vulnerable to attacks. That’s why Neumetric offers our Containers Vulnerability Assessment and Penetration Testing Services. With these services, we’ll check your containers for vulnerabilities and help you fix them so you can keep your data safe.
We’ll also identify any gaps in your container security and suggest solutions based on industry best practices. And if we find that there are no gaps—which is rare!—we’ll still provide recommendations for how to improve security even more. Our Container Security Testing includes the following Checklist:
- Container Fingerprinting
- Vulnerability Assessment
- Configuration Evaluation
- Container Scanning
- Secret Detection
- Baseline Audit
Neumetric's Container VAPT Programme
- 1. Project Onboarding and Initiation
- 3. Information Gathering
- 5. Vulnerability Assessment
- 7. Vulnerability Validation
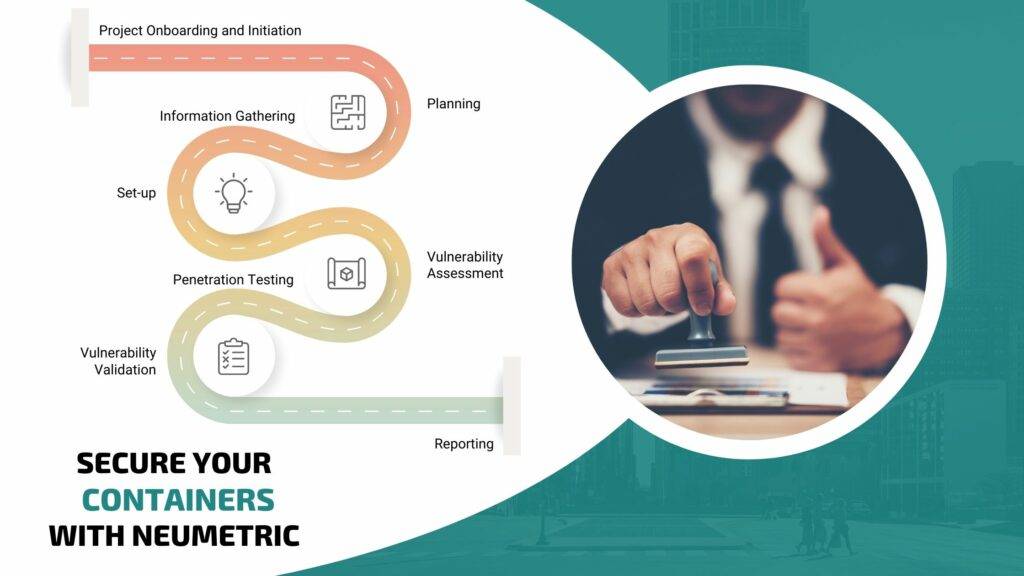
- 2. Planning
- 4. Set-up
- 6. Penetration Testing
- 8. Reporting
Our clients
Knowledge Hub
Other TechSec Services
Web Application VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Web App VAPT Testing. Check it out Now!
Mobile App VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Mobile App VAPT Solutions. Check it out Now!
VPC (Cloud) VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Cloud VAPT security. Check it out Now!
Frequently Asked Questions
If Solutions and Organisations are left un-protected or under-protected, it allows for hackers to easily access sensitive information without being observed and re-use the stolen data for wrong-doing or purposes for which the User has not given permission to.
A serious attack could result into a denial of delivery of Service, ransom demands or complete loss of Data. This will result into loss of Credibility, damage claims by Clients, loss of future Business
Technical Security and General Security.
Technical Security pertains to protection of the Platform/Product/Solution/Servers from attacks.
General Security pertains to implementing Organisation wide processes to prevent attacks from being successful
Approximately 1.25 months excluding remediation activity.
We do not remediate but do provide explanation on how to remediate the Vulnerabilities. Fixing them is your responsibility.
A container vulnerability is a security flaw that can be exploited in the software that runs on a container. Containers are designed to be secure, but due to their open source nature and frequent updates, they are vulnerable to being exploited. Some of the most common container vulnerabilities include:
- Isolation Flaws
- Untrusted Containers
- Insecure Configuration of Components
- Broken Access Control
- Insufficient Authorization
- Host-side Vulnerabilities
- Lack of Runtime Security Monitoring
- Vulnerable Container Images
- Kernel-level Vulnerabilities
- Exposed and Compromised Secrets
- Insecure Inter-Container Communication
- Inadequate Container Encapsulation
In short, if you find yourself with a vulnerable container, there are a few things you can do. First, make sure the container has been updated. If it’s not, update it immediately. Then check your dependencies and make sure they’re up to date as well.
If that doesn’t work, you may have to rebuild your image from scratch using a new base image (one that is known to be secure). This is time consuming but could be necessary if there are too many vulnerabilities in your current image.
Finally, if none of these options work for you, then you may need to consider switching from Docker or another container system altogether.
The purpose of container vulnerability scanning is to identify and remediate vulnerabilities in containers. This is important because it allows Organizations to take a proactive approach to security by identifying and patching vulnerabilities before they are exploited by attackers. It also helps ensure that containers are used in a manner that is consistent with best practices.
One challenge is the sheer number of containers an Organisation has to scan. Because they’re so lightweight and portable, containers are rapidly becoming the standard way to manage software packages in production environments. This means that there are potentially hundreds or thousands of them running at any given time, which makes it difficult for vulnerability scans to keep up with them all.
Another challenge is that many container environments are made up of several different types of containers, each with their own unique vulnerabilities and configuration options. This makes it harder for vulnerability scanners to understand how each container works as well as what vulnerabilities it might have without actually interacting with it first (which would expose sensitive data).
Finally, because containers are portable across platforms, Organisations need a way to make sure their vulnerability scanning tools work on every platform their employees use—whether that’s Windows or Linux or MacOS—so that they can find vulnerabilities before hackers do!
GRC Ecosystem
- Document Management
- Audit Management
- Risk Management
- Vulnerability Management
- Inventory Management
- Compliance Management
- Continuity Management
- Incident Management
- Education Program
Company