Table of Contents
ToggleSecuring Startup Success: Obtaining SOC 2 Report for your Business
Introduction
Service Organization Control 2 [SOC 2] is an Auditing Framework developed by the American Institute of Certified Public Accountants [AICPA] that measures a Service Organisation’s ability to protect Customer Data & maintain the privacy & security of information. SOC 2 Reports are used by Organisations to demonstrate to their Customers, Business Partners & Regulatory Bodies that they have implemented & maintained adequate controls over their data processing systems.
SOC 2 Reports help Organisations build trust with their Customers & stakeholders by providing them with assurance that the Organisation has implemented appropriate measures to safeguard their information. SOC 2 Reports are particularly important for Companies that provide services that involve storing or processing sensitive Customer Data, such as Software-as-a-Service [SaaS] providers, Cloud Service Providers [CSPs] & Data Centres.
Obtaining a SOC 2 Report provides several benefits for Businesses, including:
- Increased Customer trust: SOC 2 Reports provide Customers with assurance that their data is secure & protected, which can help build trust in the Business.
- Competitive advantage: Having a SOC 2 Report can give a Business a competitive advantage over other Organisations that do not have one.
- Improved internal controls: Preparing for a SOC 2 Audit requires Businesses to evaluate their internal controls & implement new controls where necessary, leading to improved data security & privacy practices.
- Meeting regulatory requirements: Some Regulatory Bodies require companies to have a SOC 2 Report to comply with certain Regulations, such as the Health Insurance Portability & Accountability Act [HIPAA].
- Risk mitigation: SOC 2 Reports can help Businesses identify & mitigate risks related to data security & privacy, reducing the likelihood of a data breach or cyber-attack.
Understanding the SOC 2 Report
A SOC 2 Report is a document that provides information about a Service Organisation’s controls over its information technology & data security systems. The Report is issued by an Independent Auditor who evaluates the effectiveness of the Organisation’s controls based on the Trust Services Criteria [TSC], which are a set of principles developed by the AICPA to assess the security, availability, processing integrity, confidentiality & privacy of data.
The five Trust Service Principles [TSPs] covered in SOC 2 Reports are:
- Security: This principle evaluates the effectiveness of the Organisation’s controls related to data security, such as access controls, data encryption & incident response.
- Availability: This principle evaluates the effectiveness of the Organisation’s controls related to system availability, such as system uptime, disaster recovery & Business continuity.
- Processing Integrity: This principle evaluates the effectiveness of the Organisation’s controls related to processing data accurately & completely, such as data validation & error handling.
- Confidentiality: This principle evaluates the effectiveness of the Organisation’s controls related to protecting confidential data, such as Employee & Customer information.
- Privacy: This principle evaluates the effectiveness of the Organisation’s controls related to protecting personal information, such as data collection, use & disclosure.
There are two types of SOC 2 Reports:
- SOC 2 Type I: A SOC 2 Type I Report evaluates the effectiveness of the Organisation’s controls at a specific point in time.
- SOC 2 Type II: A SOC 2 Type II Report evaluates the effectiveness of the Organisation’s controls over a period of time, typically six months to a year. SOC 2 Type II Reports are more comprehensive than Type I Reports as they require evidence of the ongoing effectiveness of controls.
Neumetric Service in Obtaining SOC 2 Report for your Business
Neumetric is a leading cybersecurity consulting firm that specialises in helping Businesses of all sizes implement effective security controls & achieve Compliance with various security Standards, including SOC 2. We understand the importance of data privacy & security in today’s digital landscape & we are committed to helping startups secure success by obtaining a SOC 2 Report for their Business.
Here are some of the ways that Neumetric can help startups achieve SOC 2 Compliance:
- Guidance on the SOC 2 process: Our team of experts can provide startups with the guidance they need to understand the SOC 2 process & what is required to achieve Compliance. This includes identifying the applicable Trust Service Principles [TSPs], defining the scope of the Audit & developing Policies & Procedures to meet the TSPs.
- Readiness assessment: We can conduct a readiness assessment to identify any gaps in the startup’s current security controls & provide recommendations for improvement before undergoing a SOC 2 Audit.
- SOC 2 Audit: We can conduct a SOC 2 Audit on behalf of the Organisation to evaluate the effectiveness of their security controls & provide an opinion on whether they are Compliant with the TSPs.
- Ongoing support: We provide ongoing support to help startups maintain Compliance with SOC 2 Standards & address any issues that arise.
- Reputation enhancement: By obtaining SOC 2 Report, startups can demonstrate to their Customers & stakeholders that they take data privacy & security seriously. This can enhance the startup’s reputation & provide a competitive advantage in the market.
Preparing for SOC 2 Audit
Before beginning the SOC 2 Audit process, it is important to define the Scope of the Audit. The Scope should be based on the services provided by the Organisation & the Trust Service Principles [TSPs] that are relevant to those services. Defining the Scope ensures that the Audit is focused on the areas that are most important to the Organisation & helps to avoid unnecessary costs & delays.
The next step in preparing for a SOC 2 Audit is to develop & implement Policies & Procedures that address the Trust Service Principles [TSPs] that are relevant to the Organisation. These Policies & Procedures should be designed to ensure that the Organisation’s controls are in Compliance with the TSPs & provide evidence of Compliance to the Auditor during the Audit.
Identifying & mitigating risks & deficiencies is another important step in preparing for a SOC 2 Audit. This involves identifying areas of weakness in the Organisation’s controls & developing strategies to address these weaknesses. This may include implementing new controls, improving existing controls, or providing additional training to Employees.
Finally, before beginning the Audit process, it is important to assess the Organisation’s readiness for the SOC 2 Audit. This involves reviewing the Policies & Procedures that have been implemented, identifying any areas of weakness or non-compliance & making any necessary changes to ensure that the Organisation is ready for the Audit.
The SOC 2 Audit Process
The SOC 2 Audit process typically involves the following steps:
- Planning: The Auditor & the Organisation work together to define the Scope of the Audit, determine the Audit timeline & identify the key personnel who will be involved in the Audit.
- Testing: The Auditor evaluates the Organisation’s controls by reviewing Policies & Procedures, conducting interviews with key personnel & testing the effectiveness of controls.
- Reporting: The Auditor prepares a Report that includes their findings, recommendations for improvement & a conclusion about the effectiveness of the Organisation’s controls.
After the SOC 2 Audit is complete, the Auditor will issue one of the following types of Audit opinions:
- Unqualified opinion: This opinion is issued when the Auditor concludes that the Organisation’s controls are effective & in Compliance with the Trust Service Principles [TSPs].
- Qualified opinion: This opinion is issued when the Auditor identifies areas of non-compliance or weakness in the Organisation’s controls.
- Adverse opinion: This opinion is issued when the Auditor determines that the Organisation’s controls are not effective & do not comply with the Trust Service Principles [TSPs].
To prepare for the SOC 2 Audit, it is important to ensure that all documentation related to the Organisation’s Policies & Procedures is up-to-date & readily accessible. Key personnel should be identified & made available to the Auditor for interviews & testing. It is also important to ensure that all Employees are aware of the Audit process & their roles in supporting the Organisation’s controls.
Some tips for a successful SOC 2 Audit include:
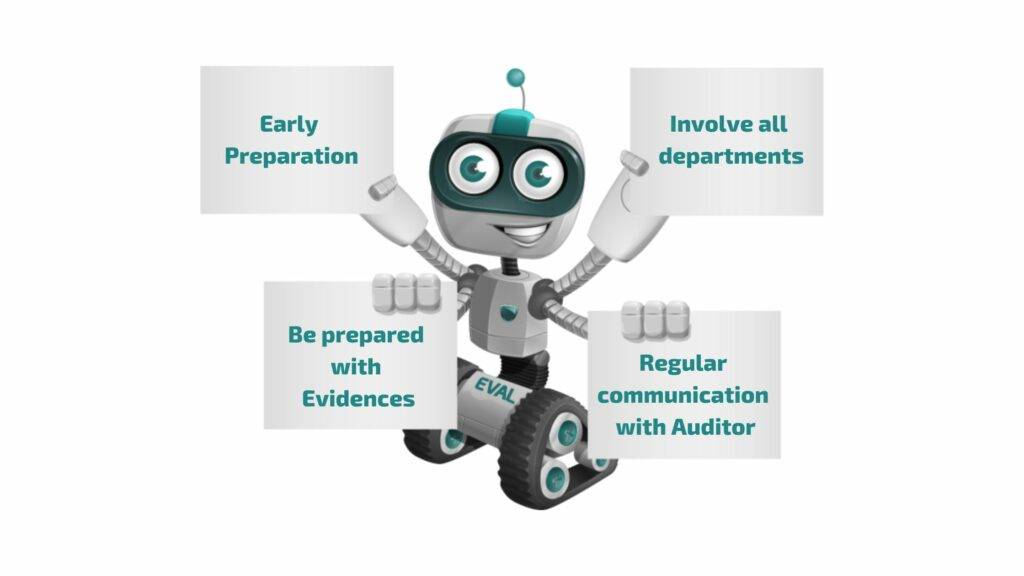
- Start the preparation process early to ensure that all necessary Policies & Procedures are in place before the Audit begins.
- Involve key personnel from all relevant departments in the preparation process to ensure that all controls are properly documented & tested.
- Be prepared to provide evidence of Compliance to the Auditor during the Audit, such as documentation, logs & other supporting materials.
- Communicate regularly with the Auditor throughout the Audit process to ensure that any issues or concerns are addressed in a timely manner.
- Be transparent with the Auditor about any areas of weakness or non-compliance in the Organisation’s controls & work together to develop strategies for improvement.
Achieving SOC 2 Report
After the SOC 2 Audit is complete, there are several steps that Organisations can take to achieve a SOC 2 Report:
- Address any issues identified by the Auditor during the Audit process & implement any necessary changes to improve the effectiveness of controls.
- Review the Auditor’s Report & recommendations for improvement & develop a plan to address any areas of weakness or non-Compliance.
- Obtain a SOC 2 Report from the Auditor, which can be used to demonstrate to Customers & stakeholders that the Organisation’s controls are effective & in Compliance with the Trust Service Principles [TSPs].
Maintaining Compliance with SOC 2 standards is an ongoing process that requires continuous monitoring, evaluation & improvement of controls. Some steps that Organisations can take to maintain Compliance with SOC 2 standards include:
- Conducting regular internal Audits to identify any areas of weakness or non-compliance in the Organisation’s controls.
- Providing ongoing training to Employees to ensure that they are aware of the Organisation’s Policies & Procedures & their roles in supporting the Organisation’s controls.
- Monitoring industry trends & updates to the Trust Service Principles [TSPs] to ensure that the Organisation’s controls remain up-to-date & effective.
Conclusion
In summary, SOC 2 Reports are an important tool for Organisations that provide services that require the protection of sensitive data. By obtaining a SOC 2 Report, Organisations can demonstrate to Customers & Stakeholders that their controls are effective & in Compliance with the Trust Service Principles [TSPs]. This can help to enhance the Organisation’s reputation, meet Regulatory & Legal Requirements & reduce the risk of data breaches & other security incidents.
We encourage Organisations that provide services that require the protection of sensitive data to take the necessary steps to obtain a SOC 2 Report. This includes defining the Scope of the Audit, developing & implementing Policies & Procedures to meet the Trust Service Principles [TSPs], identifying & mitigating risks & deficiencies & assessing readiness for the SOC 2 Audit.
While the SOC 2 Audit process can be complex & time-consuming, the benefits of obtaining a SOC 2 Report are significant. By demonstrating Compliance with the Trust Service Principles [TSPs], Additionally, SOC 2 Compliance can be a requirement for doing Business with certain Customers & partners, making it a necessary step for growth & success in some industries.
FAQs:
Who provides the SOC 2 Report?
A SOC 2 Report is provided by an independent Certified Public Accountant [CPA] or a third-party Auditing firm that is licensed to perform SOC 2 Audits. The CPA or Auditing firm evaluates the effectiveness of the company’s controls & issues a Report on their findings.
How long does it take to get a SOC 2 Report?
The timeline for obtaining a SOC 2 Report can vary depending on the complexity of the Organisation’s controls & the Scope of the Audit. On average, it can take between 3 to 6 months to complete a SOC 2 Audit & obtain a SOC 2 Report.
How much does a SOC2 Report cost?
The cost of a SOC 2 Report can vary depending on the size & complexity of the Organisation, the scope of the Audit & the Auditing firm selected to perform the Audit. The cost of the SOC 2 Report typically ranges from $15,000 to $50,000 or more. However, it is important to note that the cost of achieving SOC 2 Compliance can be significantly higher if the Organisation needs to make significant changes to their controls.
How do I get a SOC Report from a company?
To obtain a SOC 2 Report from a company, you need to first engage an independent CPA or third-party Auditing firm to perform the Audit. You will need to work with the Auditor to define the Scope of the Audit, develop Policies & Procedures to meet the applicable Trust Service Principles & identify & remediate any deficiencies or gaps in your controls. The Auditor will then evaluate the effectiveness of your controls & issue a Report on their findings, which can be used to demonstrate Compliance with SOC 2 standards to Customers, Stakeholders & Regulatory Authorities.





