



























Extensive experience in providing solutions for your Cybersecurity, Compliance, Governance, Risk & Privacy objectives!
Ensuring a robust Security Posture & Regulatory Compliance across various Frameworks & diverse Industries.
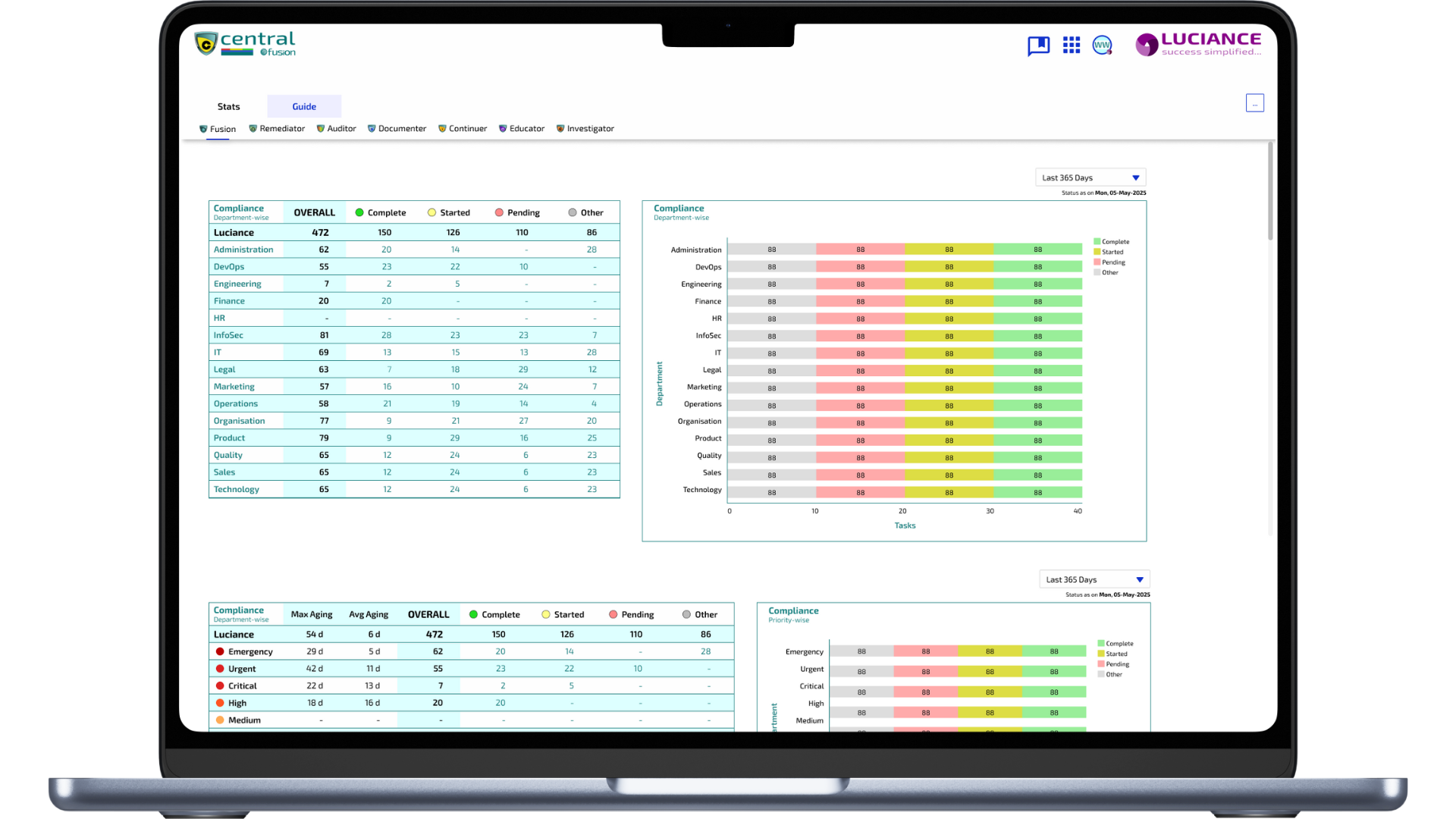
Implementing & monitoring extensive Control Frameworks tailored to your business needs…

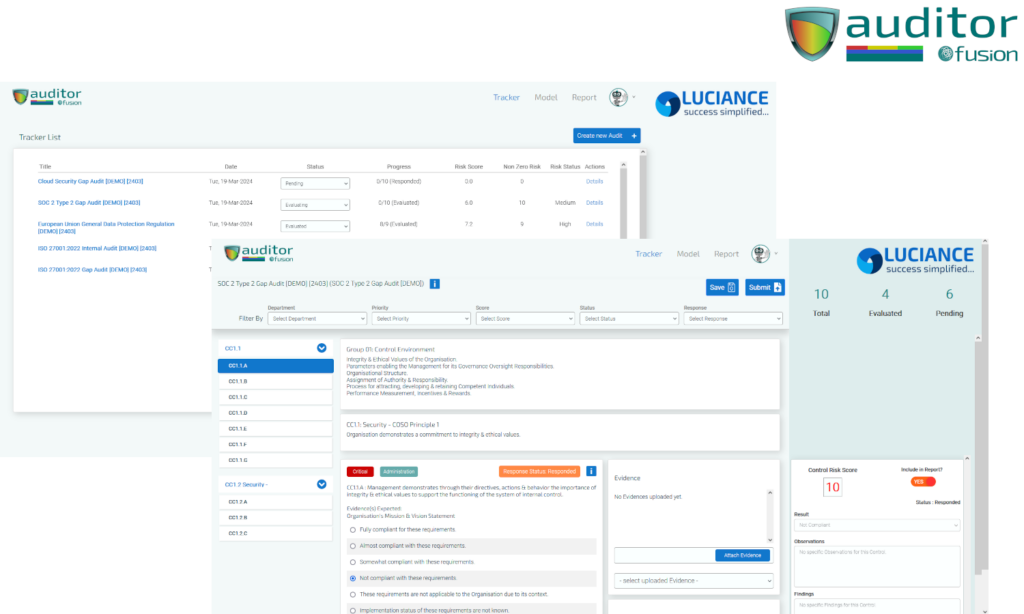
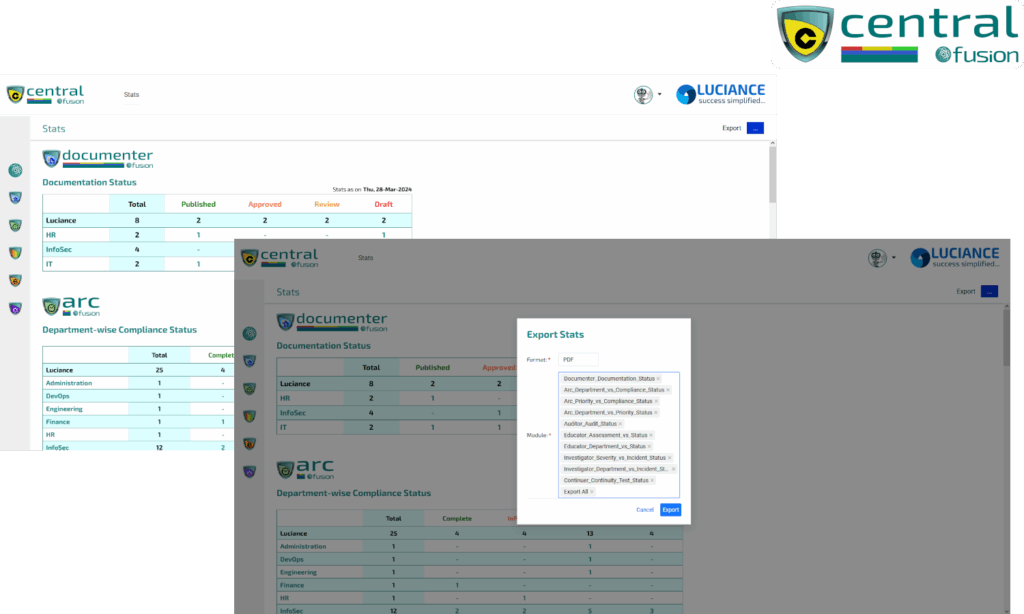
Auditor is a Compliance Assessment & Risk Management System tailored for Cyber Security Compliances & Regulations.

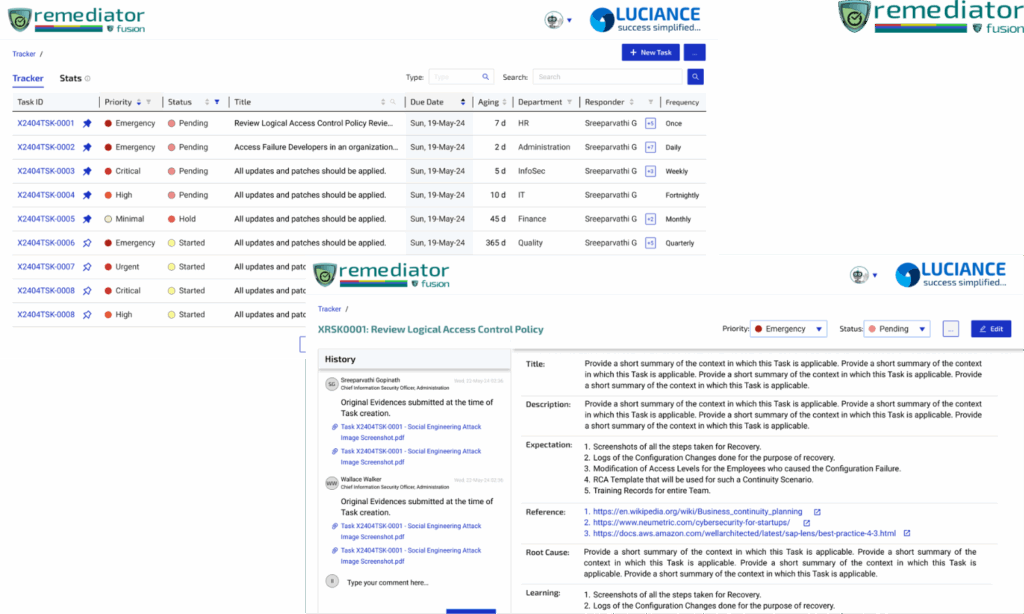
Arc streamlines compliance management with its centralized task management system, simplifying adherence to regulations.

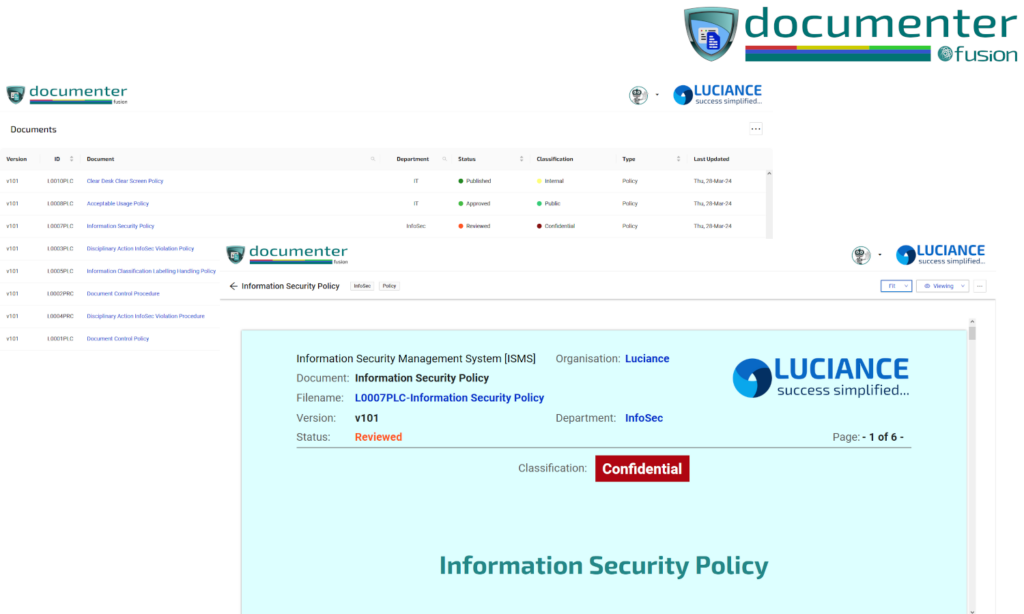
Documenter simplifies document creation & management across domains, particularly beneficial for systems like ISMS.

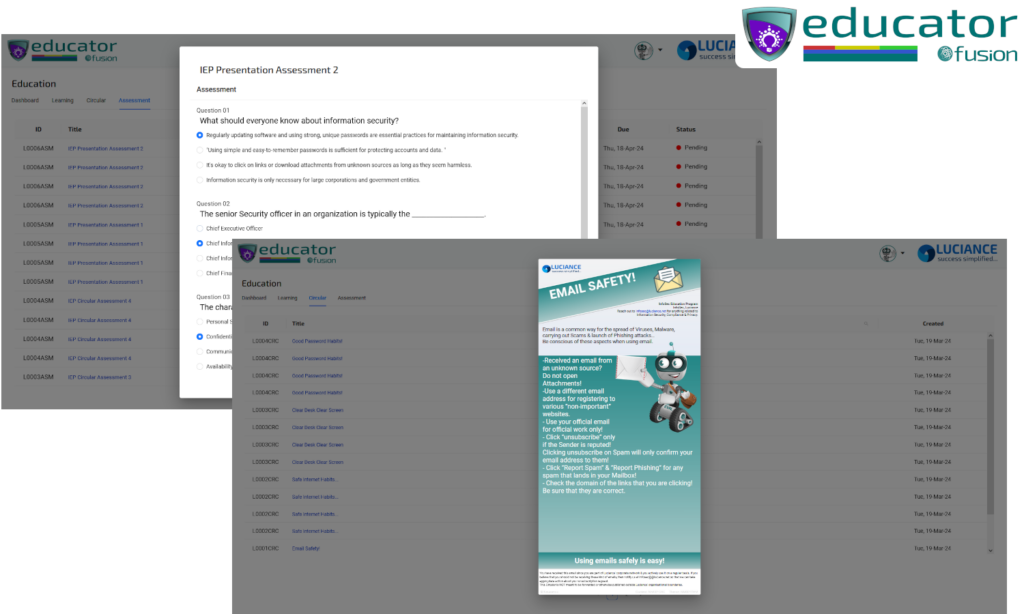
The Educator module offers comprehensive information security awareness & education programs with built-in assessments.

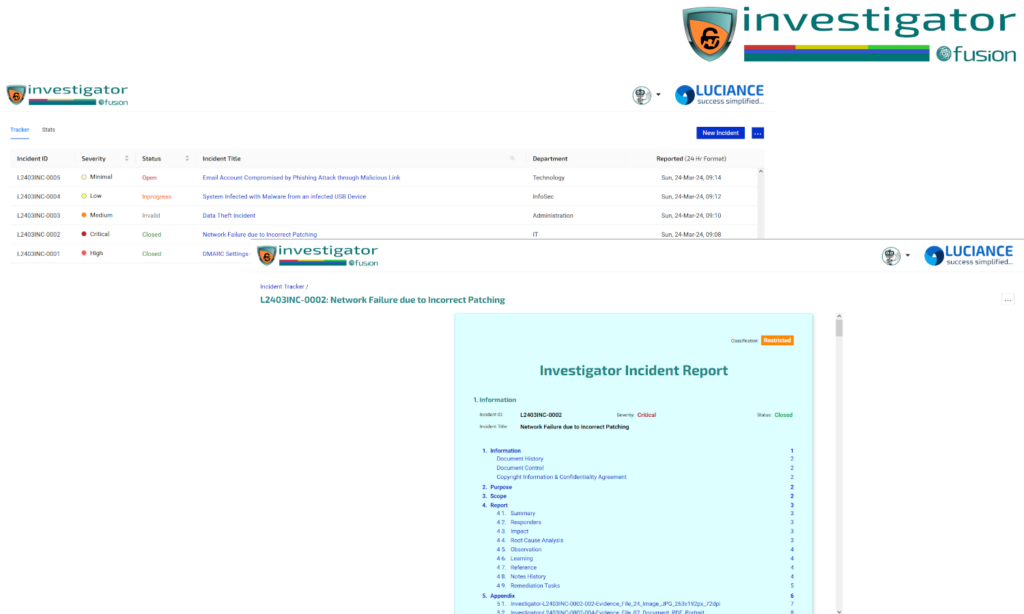
Investigator centralizes tracking, analyzing & responding to security incidents, simplifying investigations.

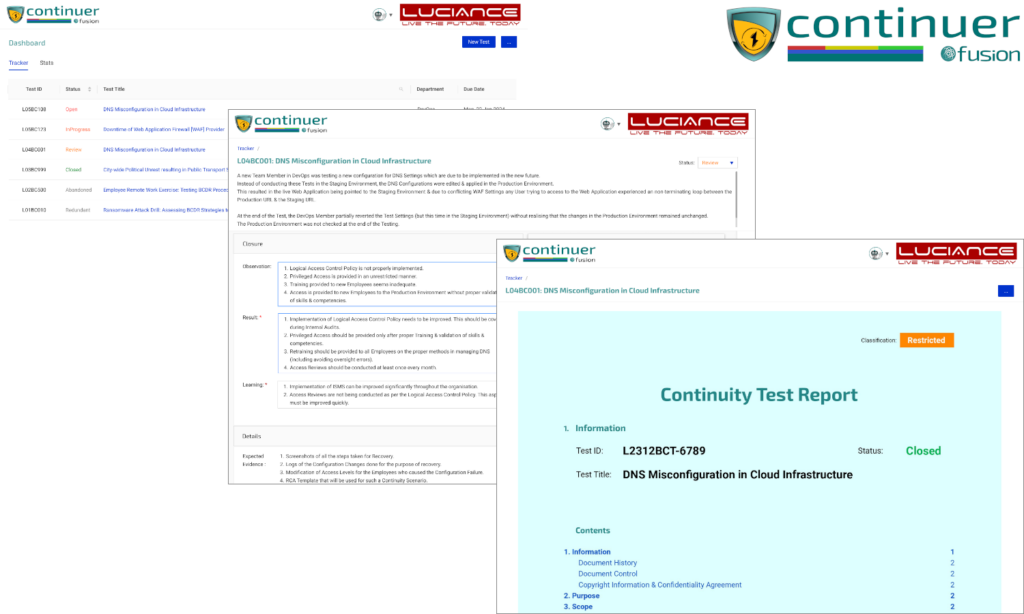
The Continuer module helps in implementing & testing a comprehensive business continuity management program.

The Educator module offers comprehensive information security awareness & education programs with built-in assessments.

The Educator module offers comprehensive information security awareness & education programs with built-in assessments.


The Educator module offers comprehensive information security awareness & education programs with built-in assessments.
Certification is an organized journey that starts with a well-planned roadmap and succeeds through effective execution across all security areas. Automation helps accelerate progress toward key milestones, making the process more efficient. Since certification is a recurring annual cycle, staying prepared ensures long-term success.

Complex compliance becomes easy with the right support. Backed by experienced security experts, organizations can simplify the process and reduce the need for maintaining a large in-house security team. We keep our Compliance and Certification Roadmaps regularly updated based on Auditor's expectations of how Security and Compliance should be managed.

Built by industry experts who understand exactly what auditors expect, ensuring seamless compliance every step of the way.


