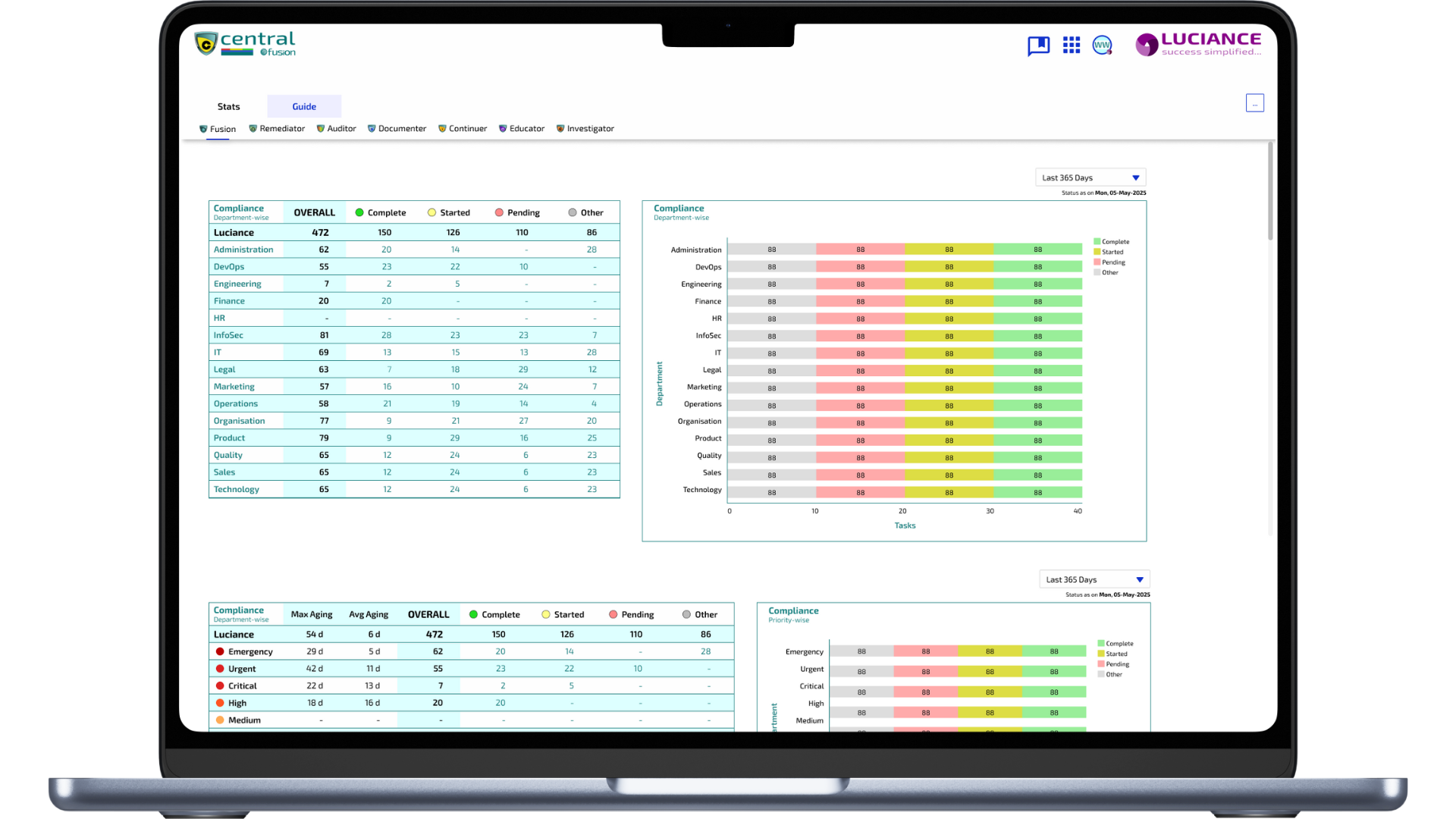




























Certification without automation is almost impossible. Compliance should be inexpensive to be effective.
We help you identify the right Certification based on your specific need and implement it in your organisation.
Vulnerability Assessment & Pen-testing for the entire range of IT Assets.
Extensive experience in providing solutions for your Cybersecurity, Compliance, Governance, Risk & Privacy objectives!
Ensuring a robust Security Posture & Regulatory Compliance across various Frameworks & diverse Industries.
Implementing & monitoring extensive Control Frameworks tailored to your business needs…
Vulnerability Assessments & Pentesting for the entire range of IT Assets
Obtain Consultation & vCISO from experienced & certified Security Experts.
Outsource your Security Function. Offload your security & compliance worries...


